Learn, Do, Secure
The internet is the world's largest network system. It processes billions of online transactions each day and connects millions of computers to carry out these transactions. Unfortunately, it is also the largest network platform used by cybercriminals to carry out thousands of cyberattacks each day.
Large organizations are not the only targets of cyberattacks, small and medium-size organizations, and individuals are increasingly becoming targets of ransomware (a type of cyberattack that encrypts or steals data and demands a monetary ransom before the data is decrypted and available to the data owner, or not exposed on the internet).
As we use the internet to carry out work and personal activities, it is important that we are cyber smart by following simple but very helpful tips to protect work and personal data, and our devices when online.
The following are some helpful tips:
Protect Your User Account
Your user account is the gateway to the IT resources you use and the first line of defense against unauthorized access. It is important that you keep your user account secure by protecting your login details.
- Your NEIU user ID and password must not be used to register accounts on any IT system that you use for personal purposes. Separate the use of your NEIU login details from personal login details. It keeps you and the University safer.
- Make your password strong and don't share. Remember, UTS will never ask you for your login details whether on campus or when working remotely.
- Don’t use the same password on multiple IT systems. If your password to one IT system is compromised, your accounts to other systems could be compromised too if you use the same password.
- If you must communicate a password in writing or verbally, ensure the password is not susceptible to unauthorized access and/or cannot be linked to the account or document it is protecting.
- Do not communicate a password in the same email containing the user ID or document it is protecting. Communicate the password verbally, via text message, or in person if possible. When communicating a password verbally, do so privately to prevent eavesdropping.
- When you receive a password to a document, memorize the password and destroy or delete the written record of the password. Reset the password to a user account immediately after your first log in.
- Learn more about password management in the University’s Password Policy.
- Learn more about managing and protecting your NEIU user account.
Use Multi-factor Authentication (MFA)
MFA is designed to provide an additional layer of security when you want to log into an IT system. It works by requiring you to verify yourself in addition to your user ID and password during authentication. If MFA is available to use, we advise that you enable it for your user account to provide additional security.
Learn more about the University’s multi-factor authentication implementation.
Don't Be Phished
Phishing is a tactic used by cybercriminals to trick people into believing a message or information to make them divulge sensitive information or click on a malicious link. This could then be used by cybercriminals to carry out fraudulent or harmful activities, including gaining unauthorized access to IT systems and information, impersonating individuals for financial gain, carrying out a ransomware attack, etc.
- If you are unsure about a message you receive, think and do not click a link or download an attachment included in the message until you are sure it is from a genuine source. Do the following:
- Ask yourself if you were expecting the email from the sender or that type of email at all.
- Check the name of the sender and email address carefully. Are the name and address spelled correctly?
- Does the email address match their organization exactly? Watch out for misspelled words and unusually lengthy or extra characters in the email address.
- Don’t panic or be quick to take an action. Ask yourself if you are being rushed to take any action or do something unusual like providing personal or sensitive information, making a purchase, changing a setting on your device, etc.
- Check the website address (URL) by mousing over the link in the email to see where it leads. Don't be deceived because it has "HTTPS." You should search for the correct web address of that organization using a search engine such as Google.
- If you suspect or believe it is a spam or phishing email, select the three dots next to the Reply button in the scam email and choose "Report Phishing" or “Report Spam” to alert Google’s software engine to learn this and take the necessary steps to stop it. Also, report it to abuse@neiu.edu.
- Be careful when you visit websites and watch out for things that could indicate a website is not secure or is bogus. Check for:
- The correct name and/or spelling of the website. Check for unusual characters in the address. Don't be deceived because it has "HTTPS." If you are not sure, use a search engine such as Google to search for the organization and its website address.
- Any difference or change in the look of the website to the one you are familiar with.
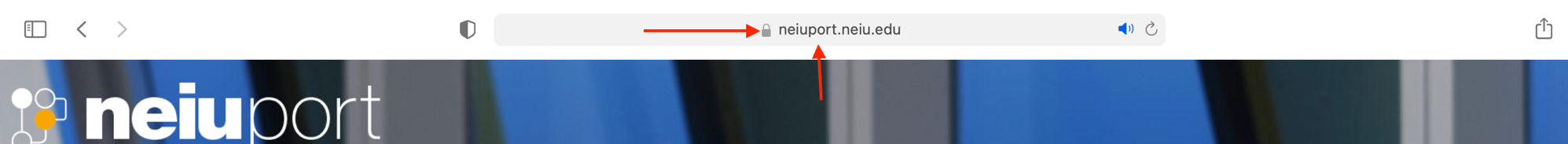
- A padlock icon that shows that the website is secure. Click on the padlock icon to learn more about the website’s security. See the image below as an example.
- If you accidentally clicked on a link in a phishing email and your device appears to be infected with malware, use anti-virus software to check and clean your device and contact the UTS Help Desk as soon as possible for further help.
- If you accidentally responded to a phishing email and provided your password, change your password immediately. Also, check with the UTS Help Desk for further help.
Use Secure Wi-Fi
- Make sure your Wi-Fi at home is secured with a password. Change the default password and use a strong one.
- When you are on the move, use secure Wi-Fi (the one that requires a password) or use your Personal Hotspot. Don’t just connect to any Wi-Fi because it is free.
- If you must use unsecured Wi-Fi, avoid accessing any sensitive University applications, or use NEIU VPN to protect your network activities. Also, you should avoid accessing other systems such as your online banking or retail accounts, etc. You never know who is connected to the unsecured Wi-Fi to capture information as it passes over the network.
Protect Data
Handle and store information securely. Consider how you handle and store it. Would the way you store, or handle information make it susceptible to an unauthorized person accessing it?
- Don’t share sensitive information just for the sake of doing so. If you must share information, share what is only needed and on a need-to-know basis. Unlawful use or sharing of work information could result in negative consequences to the University and you.
- Store and back up University information on University-approved storage areas (not your personal Google Drive, Office 365, iCloud, or Dropbox, etc) to comply with the University's policies and related legislation.
- Avoid storing non-work information in University storage systems. The University has the right to access and monitor any information stored in its systems.
- If you must store information on a mobile device e.g., laptop, iPad, or tablet, make sure the device is password protected. Where possible, the hard disk of the laptop should be encrypted, or use encrypted USB drives. (Encryption is when information is scrambled and unreadable to prevent unauthorized access to it unless you have the right password to decrypt it, i.e. make it readable).
- Check the permission requests from apps before allowing any apps to have access. Don’t just click accept or yes to any app requests. You may be giving cybercriminals access to all your data including University data.
- Store, handle and dispose of University data securely including paper copies of sensitive information. Contact the Help Desk for help with deleting or disposing of information.
- Handle and store your personal information in ways that assure you it is protected from unauthorized people.
Protect Mobile Devices
Consider how you handle mobile devices (laptops, mobile phones, iPad, tablets, etc).
- Ensure that the software (operating systems and apps) on your device are up-to-date to protect against new software vulnerabilities. Enable automatic software update on your device.
- Enable device pin or passcode screen lock on portable devices to prevent unauthorized access.
- Password-protect your computer. Use a strong password and don't share.
- Set up your device to automatically lock its screen after a period of inactivity (ideally 15 minutes) to prevent unauthorized access to information.
- Enable firewall on your device to block unwanted network traffic.
- Download apps only from approved apps stores to avoid downloading malicious apps.
- Install anti-virus software on your device and keep it up-to-date to protect against malware infection. University devices have anti-virus software installed. You can purchase anti-virus for your personal device at a discount from neiu.onthehub.com.
- Enable your device to wipe data off remotely should you lose it.
- Don't jailbreak your device for your convenience (Jailbreaking is removing the manufacturer’s software restrictions). This makes your device susceptible to hacking.
- Don't leave your devices unattended in public areas. Lock them away if not in use.
- Ensure you delete all data and apps securely and do a factory reset before gifting or disposing of a device. For University devices, contact the UTS Help Desk for guidance.
Maintain Security in Remote and Mobile Working
Take extra care when you are working away from your normal working environment or home.
- Use only secure Wi-Fi (the one that requires a password) to ensure your activity on the network is protected.
- Use VPN if you must access sensitive work applications remotely.
- As much as possible, keep your computer screen from public view to prevent shoulder surfing.
- When you are in a public place like a coffee shop, lock your computer screen and take your laptop or other mobile devices with you even if you must step away briefly.
- Use encrypted devices if you carry work or personal information with you on small devices like USB drives. Small devices are highly susceptible to loss or theft.
- Put sensitive documents away if not in use to protect them from unauthorized access.
- When you are working in a place like a coffee shop, check your environment properly before you leave to be sure nothing important is left behind.
Use Social Media Safely
When you use social media sites, you are responsible for what you share and who you share it with. You are also responsible for managing your social media account safely to keep your information and what you share private.
- Do not use your work email to register a personal account on social media sites.
- Check with the Division of Marketing and Communications if you need a social media user account for work. See the University's Social Media Practices and Procedures for more information.
- Use strong passwords (not your University passwords) for your social media account and change your password periodically.
- Think twice before you post any information or pictures that you wouldn't want your family, friends or employers to see.
- Remember, once you post a message, it is out of your control even when you delete it. Some features used by social media sites keep your information online for some time based on their retention policies. Anyone might be able to see, share, store or use it.
- Be careful what information (either work or personal) you share on social media sites. Hackers use social media platforms as tools for gathering information that could be used against you or the University. Don't share any information that could be used to impersonate you.
- Make sure you stay up to date on the privacy guidelines and enable privacy settings provided by social media sites to keep your information private.
- Be careful who you connect with on social media. If you are not sure of a friend or a professional connection request, don't accept it.
- Keep your social media posts tidy. Delete posts including pictures you think should no longer be there.
- Delete your social media account if it's no longer needed.